 Saturday, May 11, 2019 in Security Saturday, May 11, 2019 in Security  No Comments No Comments |  | The Russia-linked threat group known as Turla has been using a sophisticated backdoor to hijack Microsoft Exchange mail servers, ESET reported on Tuesday.
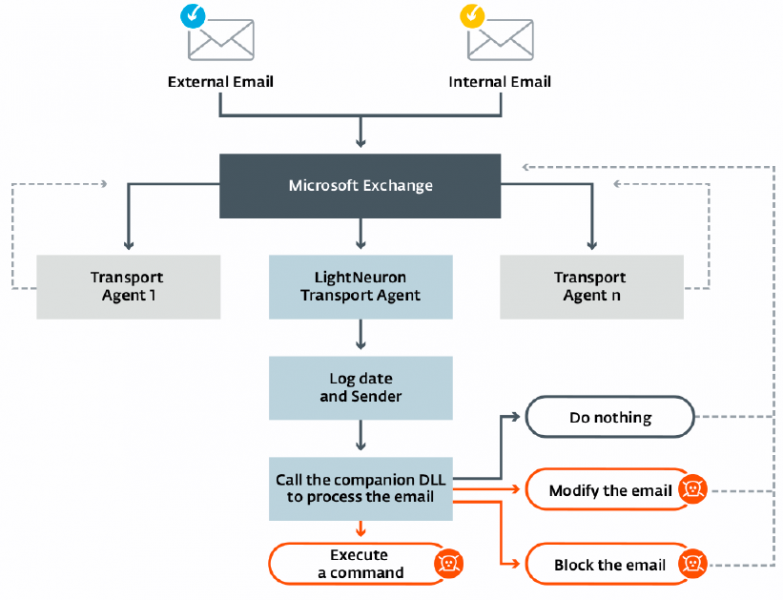
The malware, dubbed LightNeuron, allows the attackers to read and modify any email passing through the compromised mail server, create and send new emails, and block emails to prevent the intended recipients from receiving them.
According to ESET, LightNeuron has been used by Turla "the group is also known as Waterbug, KRYPTON and Venomous Bear" since at least 2014 to target Microsoft Exchange servers. The cybersecurity firm has analyzed a Windows version of the malware, but evidence suggests a Linux version exists as well.
ESET has identified three organizations targeted with LightNeuron, including a Ministry of Foreign Affairs in an Eastern European country, a regional diplomatic organization in the Middle East, and an entity in Brazil. ESET became aware of the Brazilian victim based on a sample uploaded to VirusTotal, but it has not been able to determine what type of organization has been targeted.
The company`s researchers have determined that LightNeuron leverages a persistence technique not used by any other piece of malware, a transport agent. Transport agents are designed to allow users to install custom software on Exchange servers.
The malware runs with the same level of trust as spam filters and other security products, ESET said.
securityweek.com | |
|